This feature is only available on Chainloop’s platform paid plans.
- Create a product and attach the SLSA framework to enable compliance tracking.
- Create and configure workflows and projects for both source track and build track validation.
- Verify SLSA compliance for your source code and build environment using Chainloop platform.
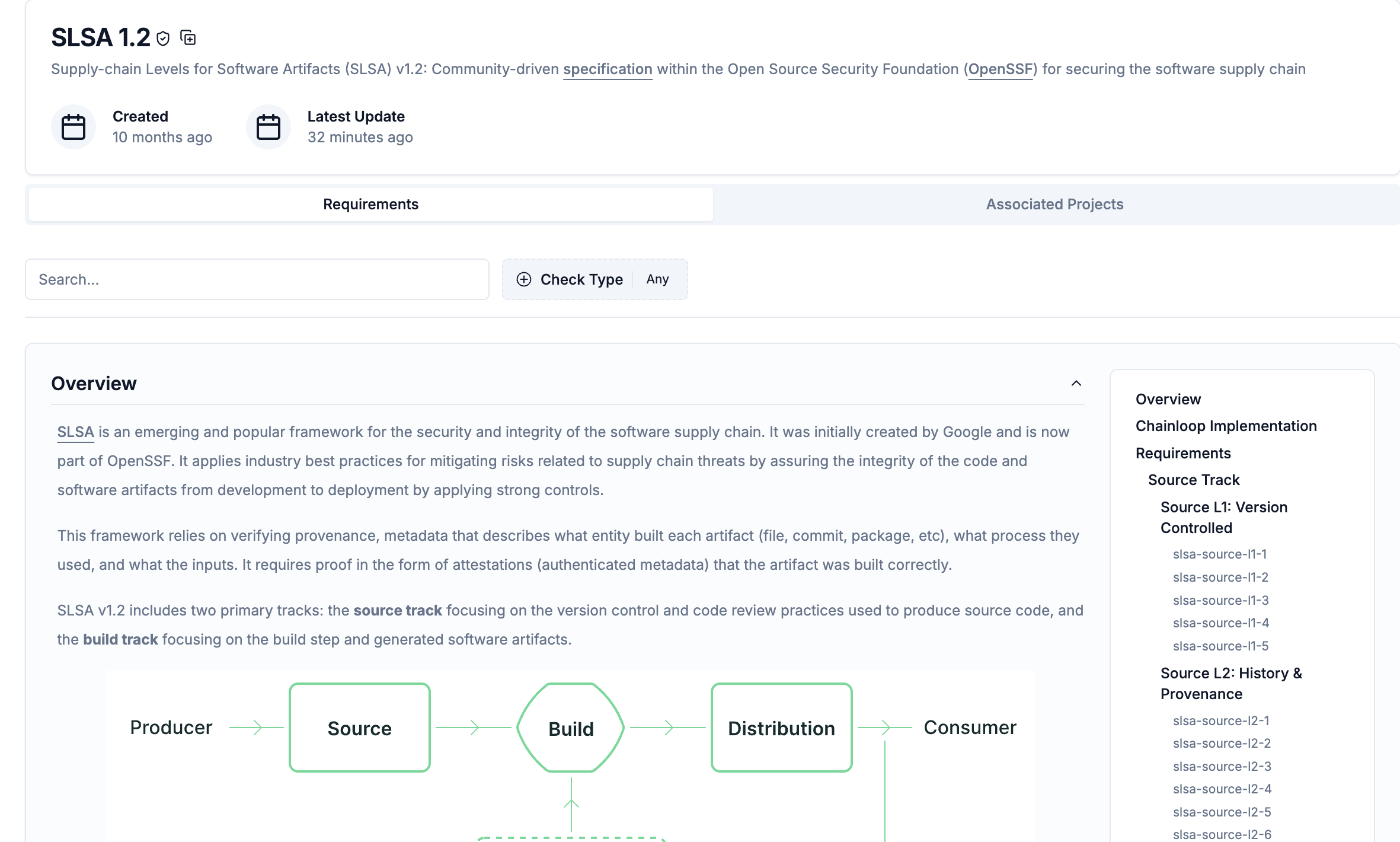
1 - Create Product and Attach SLSA Framework
Before configuring workflows, you need to create a product and attach the SLSA framework to enable compliance tracking. Frameworks are attached at the product level, not the project level.Create a Product
Create a product that will contain your projects and have the SLSA framework attached (full docs available here):- Go to the Web UI and create a new product
- Name: Unique name for your product (e.g., “Skynet Platform”)
- Description: Description of what the product encompasses
Attach SLSA Framework
Once you have a product, attach the SLSA framework to it (full docs available here):- Attach Framework: Add the SLSA 1.2 framework to your product
2 - Create and Configure Workflows and Projects
This step involves creating workflows for both tracks, attaching the project to your product, and configuring attestation processes. We assume you already have the chainloop command line tool available (installation docs).Step 2.1: Create Workflows and Project
Create Chainloop workflows for both source track and build track validation. Both workflows will use the same projectskynet, which will be automatically created:
Build Track Workflow
Replace “skynet” with your actual project name and “cyberdyne core” with your team name. This example uses “skynet” consistently throughout the guide.
GitLab users: If you’re using GitLab CI, download the contract file and update the runner type from
GITHUB_ACTION to GITLAB_PIPELINE before applying it.Source Track Workflow
GitLab users: If you’re using GitLab CI, download the contract file and uncomment the runner section, changing it from
GITHUB_ACTION to GITLAB_PIPELINE.The contract name follows the pattern
{project-name}-{workflow-name}. Since we created workflows for the “skynet” project, the contracts are named skynet-build and skynet-source-code.Step 2.2: Attach Project to Product
After creating your workflows (which automatically created theskynet project), attach it to your product:
- Go to the products page in the Web UI
- Select your product (created in step 1)
- Click “Edit Product”
- In the “Projects” section, attach the automatically created project:
skynet(created by the workflows above)
- Save the changes
Step 2.3: Send Attestations to Chainloop
Configure attestation processes for both tracks to continuously validate SLSA compliance.Build Track Attestations
Configure your CI workflow to perform runner verification and send build attestations:- GitHub Action
- GitLab Pipeline
Add Then perform regular attestation process in your build pipeline.
id_token write permission to your GitHub workflow file:Source Track Attestations
Set up periodic GitHub or GitLab actions for continuous source compliance monitoring:- GitHub Action
- GitLab Pipeline
Create
.github/workflows/slsa-source-validation.yml:The
gather-runner-context command collects comprehensive repository security configuration data including:- Branch protection settings (admin enforcement, push restrictions, deletion controls, and linear history requirements)
- Pull request protection (review requirements, conversation resolution, and dismissal rules)
- Commit protection (signing requirements)
- Repository access settings (team access and custom roles)
3 - Verify SLSA Compliance
Now that you are generating SLSA provenance and source track attestations through your configured workflows, you can monitor SLSA compliance in Chainloop. The SLSA framework attached to your product (configured in step 1) will automatically evaluate both automated policies and manual requirements.View SLSA Compliance Status
Go to your project in the Chainloop platform to view compliance status:- Navigate to your project (e.g., “skynet”)
- Go to the Frameworks section
- View the SLSA 1.2 framework compliance status
- Build Track: Requirements automatically validated through your build workflows with signed provenance
- Source Track: Requirements automatically validated through your source validation workflows with repository security configuration data
By default, Chainloop runs in ADVISORY mode for policy violations, meaning failing policies won’t block attestation submission but will be flagged for review. This allows you to identify compliance gaps while maintaining development velocity. Policy violations can be configured as ENFORCED to block attestations when policies fail.
Manual Evidence and Configuration Confirmation
In addition to the automated validations from your workflows, SLSA compliance requires manual confirmation of:- Organizational processes (e.g., code review practices, access control policies)
- Security configuration verification (e.g., multi-factor authentication enforcement, build platform isolation)
- Documentation of security controls (e.g., evidence files for strong platform controls)
4 - Troubleshooting
When working with SLSA attestation you might run into the following errors:Runner not Authenticated
Chainloop will report that runner is not authenticated or that the workflow file path is missing when the OIDC token can’t be retrieved. The errors that you might see in your SLSA policies execution are:Runner is not authenticatedRunner workflow file path is missing or is empty
- GitHub
- GitLab
When using GitHub Actions, make sure that the
id_token permission is set on the workflow level, not job level. For example:Runner Environment is not Valid
Chainloop will report that runner environment is not valid when the runner environment is not as the one provided in the policy. This means that the build runner platform is not as expected. The expected and actual runner platform are provided in the error message. The errors that you might see in your SLSA policies execution are:Runner environment is not valid
Keyless Signatures not Supported
Chainloop will report that keyless signatures are not supported when the provenance is not signed. Verify that your build platform is using the newest version of Chainloop. The errors that you might see in your SLSA policies execution are:Keyless signing configuration is invalid or not found

