This feature is only available on Chainloop’s platform paid plans. Roles
Organization roles
There are five organization level roles:
- Organization Owner: It’s the highest privilege role, providing full access to all resources and features. It’s the role acquired by the creator of the organization.
- Organization Admin: It’s a management role in the organization, they have full access to the organization, its members and projects.
- Organization Viewer: It’s a read-only role that provides full visibility on the organization resources.
- Member: Members can create projects. They only have permissions in projects they create, or they have been added to with a Project Role. Members can manage projects but cannot manage organization resources.
- Contributor: Contributors can only contribute to projects they have been added to with a Project Role. Contributors cannot create projects and cannot manage organization resources.
Organization access summary:
| Role | Org Access | Can Create Projects | Project-scoped RBAC |
|---|
| Organization Owner | Full Access | Yes | Admin on all projects |
| Organization Admin | Full Operations Access | Yes | Admin on all projects |
| Organization Viewer | Read-only | No | Viewer on all projects |
| Member | Limited | Yes (*) | Depends on project role |
| Contributor | Limited | No | Depends on project role |
Org Owner, Admin and Viewer roles can operate on all projects in the organization. While Members and Contributors can only operate on projects they have been added to with a Project Role.
Product roles
Product roles are used to manage user access at the product level, which is a collection of projects. There are two product roles:
- Product Admin: Provides full access to the product, including managing projects, attaching compliance frameworks,
and managing user access.
- Product Viewer: Provides read-only access to the product and its associated projects.
Note that product roles will be propagated to the projects associated with the product, but they do not override project roles.
For example, a Product Viewer will still have read-only access to the projects, but if they have a Project Admin role on a specific project, they will have full access to that project.
Project roles
Project roles are needed when the user has the Organization “Member” or “Contributor” role to define their access level to specific projects. There are two different project roles:
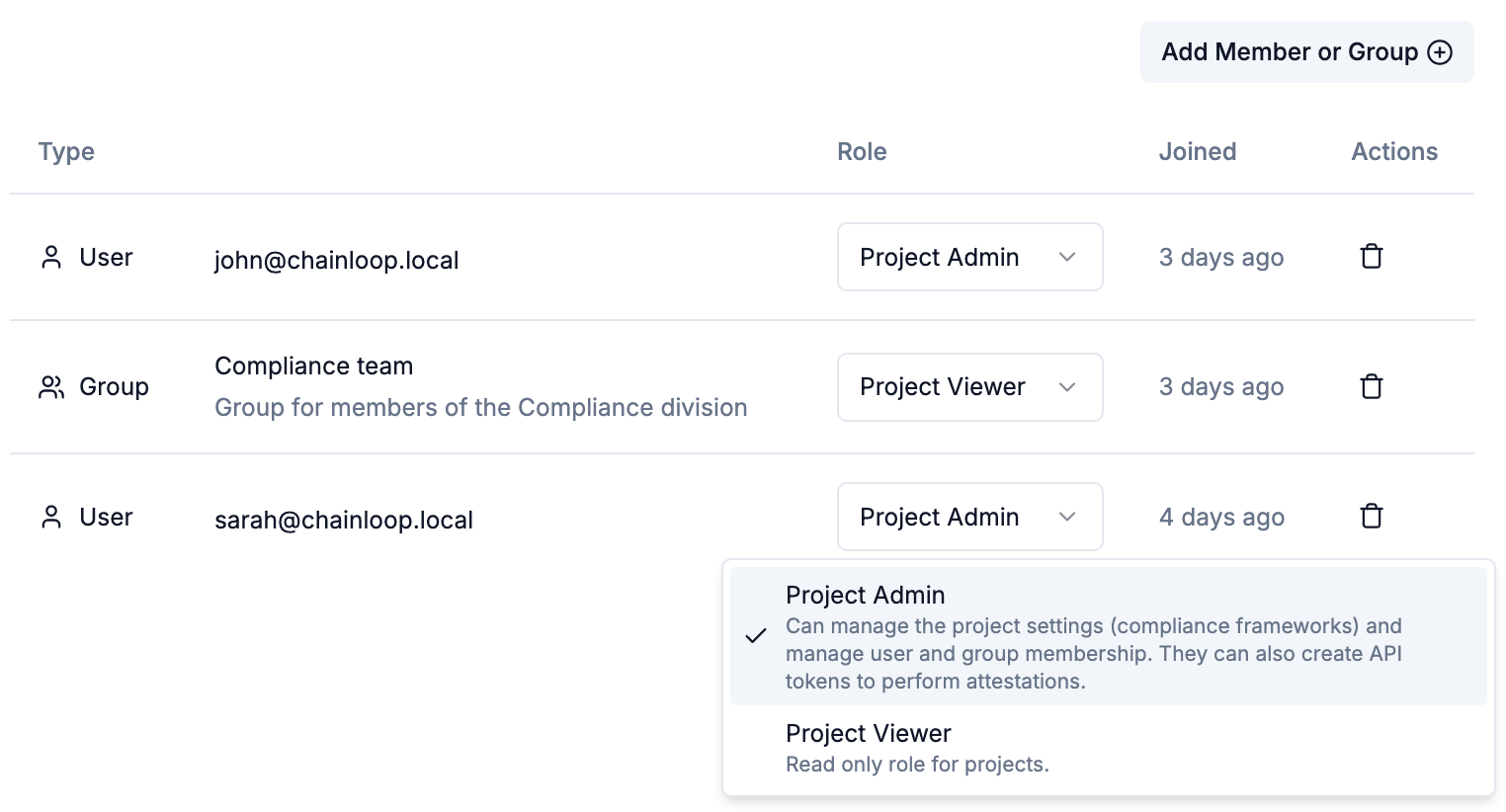
- Project Admin: Provides full access to the project resources. For example, they can manage workflows, create project-scoped contracts, configure compliance frameworks, and user or group membership. They can also create project API tokens and perform attestations.
- Project Viewer: Provides read-only access to the project, workflows, and attestations.
Assigning product and project roles
You can list and manage members through products or project settings:
 Then you can use the membership form to add members and assign them project roles:
Then you can use the membership form to add members and assign them project roles:
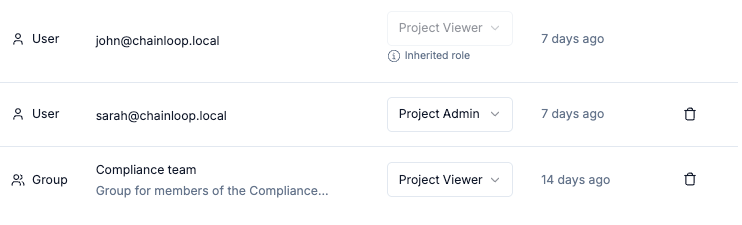
 Propagated roles will be shown grayed out, indicating that they are inherited from the product level.
Propagated roles will be shown grayed out, indicating that they are inherited from the product level.
Groups
Groups can help in organizing users by Business Unit, Teams, Department, or any other criteria.
They can be attached to projects with a given role. Users of the group would acquire that role when accessing the project.
Creating groups
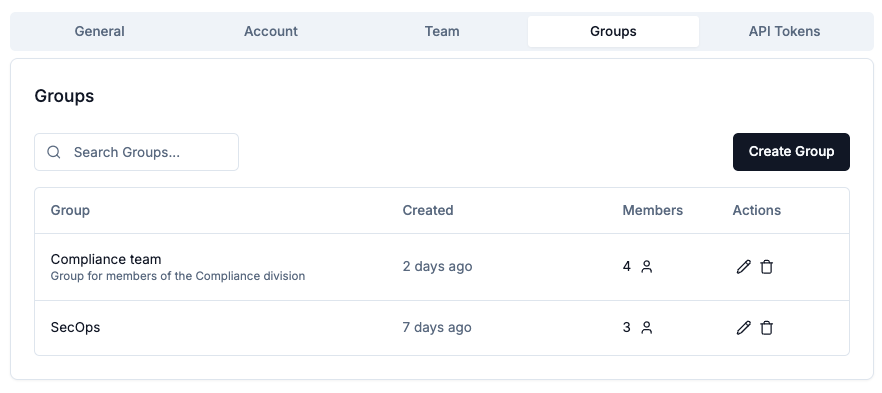
Only Organization Admins can create groups through the “Groups” section in Organization settings:
Adding users to a group
In Group Details view, Admins can add new members to an existing group by clicking the “Add Member” button:
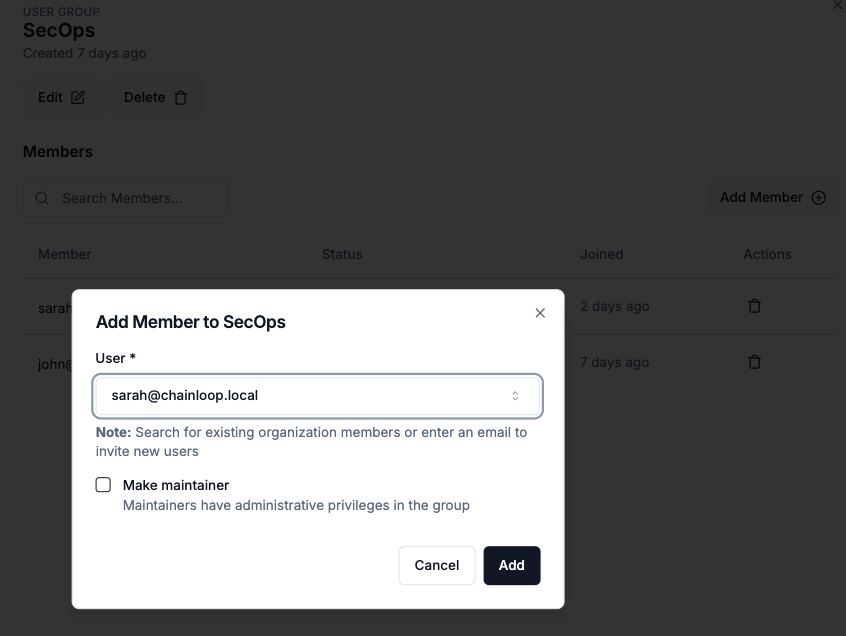 Group “Maintainers” can add and remove members from the group, regardless of their Organization Role.
Group “Maintainers” can add and remove members from the group, regardless of their Organization Role.
Project-scoped API tokens
Alongside org-level API tokens, project-scoped API tokens can now be created from the project settings:
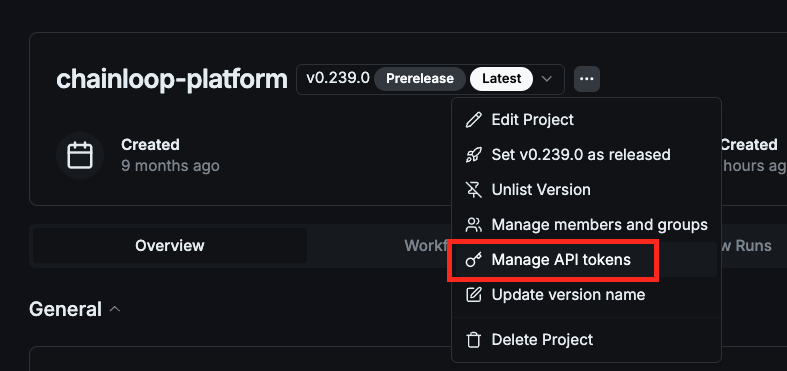 These tokens can be used to authenticate the Chainloop CLI/API, perform attestations, or operate in the context of a specific project. This adds security guarantees that a team can’t interfere with another team’s project and removes the bottleneck of requiring an organization administrator to provide such tokens.
These tokens can be used to authenticate the Chainloop CLI/API, perform attestations, or operate in the context of a specific project. This adds security guarantees that a team can’t interfere with another team’s project and removes the bottleneck of requiring an organization administrator to provide such tokens.
Summary of RBAC permissions
Here you can find a summary of all the permissions (Read, Read/Write) associated with each role and resource.
Org-level resources
| Resource | Org Admin / Owner | Org Viewer | Org Member | Org Contributor | API tokens |
|---|
| API tokens | RW | R (1) | | | |
| Artifact | RW | R | RW | RW | |
| Audit logs | R | | | | |
| Business Units | RW | R | R | R | |
| Contracts | RW | R | R | R | RW (6) |
| Frameworks | RW | R | R | R | |
| Integrations | RW | R | R | R | |
| Memberships (4) | RW | R | R | R | |
| Org settings | RW | R | R | R | |
| Organization | RW (3) | R | R | R | |
| Policies | RW | R | R | R | |
| Requirements | RW | R | R | R | |
| Repositories | RW | R | R | R | |
| Signing certificate | R | R | R | R | R |
| Storage backend | RW | R | R | R | |
| User group | RW (5) | R | R | R | |
Product/project level resources
| Resource | Org Admin / Owner | Org Viewer | Org Member | Org Contributor | Product Admin | Product Viewer | Project Admin (2) | Project Viewer | API tokens |
|---|
| Attestation | RW | R | | | | | RW | R | RW |
| Comments | RW | RW | | | RW | RW | RW | RW | |
| Compliance Data | RW | R | | | RW | R | RW | R | R |
| Contracts | RW | R | | | | | RW | R | RW (6) |
| Discover (graph) | R | R | | | | | R | R | |
| Evidence | R | R | | | R | R | R | R | R |
| Files | RW | | | | | | RW | | |
| Integration attachments | RW | R | | | RW | | RW | | |
| Products | RW | R | | | RW | R | | | R |
| Projects | RW | R | | | | | RW | R | RW |
| Workflow Metrics | R | R | | | | | R | R | |
| Workflow Run | RW | R | | | | | RW | R | |
| Workflows | RW | R | | | | | RW | R | RW (6) |







