Overview
Policies are rules evaluated against materials and/or the whole attestation document. They represent acceptance criteria for the system to ingest those materials. Even in failure cases (when there are policy violations), attestations are still sent to Chainloop but marked as “not compliant.” This way, Chainloop keeps track of everything happening in the system, even if it’s unacceptable. Policies are written in Rego language. Policies are also a fundamental piece in Chainloop’s compliance platform, as they are directly related to framework requirements. With the assistance of SecOps and developers, Requirements are matched to specific logic in Policies (programmed) written in the OPA Rego language. Rego is a rule engine and language used to automate the analysis of different reports and inputs to the system. Policies can also be grouped into Policy Groups to facilitate reuse across different products. For instance, a SAST (static application security testing) policy group can consist of a “no-vulnerabilities” policy, a “CWE” policy for common weaknesses, and a “secrets detection” policy.Policy types
Policies can be of two types:- Built-in: policies that are part of the Chainloop platform
- Custom: policies that are created and stored in the Chainloop platform
Built-in policies
Chainloop provides a curated set of policies tailored to common compliance controls, like:- SBOM sanity checks,
- Artifact signature verification,
- Licenses and component versions ban policies
- SAST, linters result checks, code quality and coverage
- CVE scans,
- etc.
Custom policies
Custom policies are policies created by the user that can be stored in the Chainloop platform or in a local or remote file.Using Policies
Attaching policies to a contract
Policies are attached to a contract via thepolicies section. Policies can be applied to any material, but also to the attestation statement as a whole.
Option 1 - By reference
You can reference policies via three methods:- If it’s a policy stored in the Chainloop platform (either built-in and custom), you can reference it by name
- If it’s a custom policy, you can reference it by URL or by path
To store a custom policy in the Chainloop platform, see Store Custom Policy.
-
(1) is a built-in policy referenced by name. Since that policy is compatible with
SBOM_CYCLONEDX_JSON, only SBOM materials (sbomandanother-sbomin this case) will be evaluated against it. If we wanted to only evaluate the policy against one specificsbommaterial, and skip the other, we should filter them by name:Here, we are making explicit that onlysbommaterial must be evaluated by thesbom-banned-licensespolicy. -
(2) the attestation in-toto statement as a whole will be evaluated against the remote policy
my-custom-remotepolicy.yaml, which has atypeproperty set toATTESTATION. This brings the opportunity to validate global attestation properties, like annotations, the presence of a material, etc. You can see this policy and other examples in the examples folder.
chainloop attestation add commands, while attestation policies are evaluated in chainloop attestation push command.
Option 2 - Embedded
As an alternative to referencing policies, you can also embed them in your contract. This is useful if you want to ensure that the policy source cannot be changed, as it’s stored and versioned within the contract.Understanding policy evaluation results
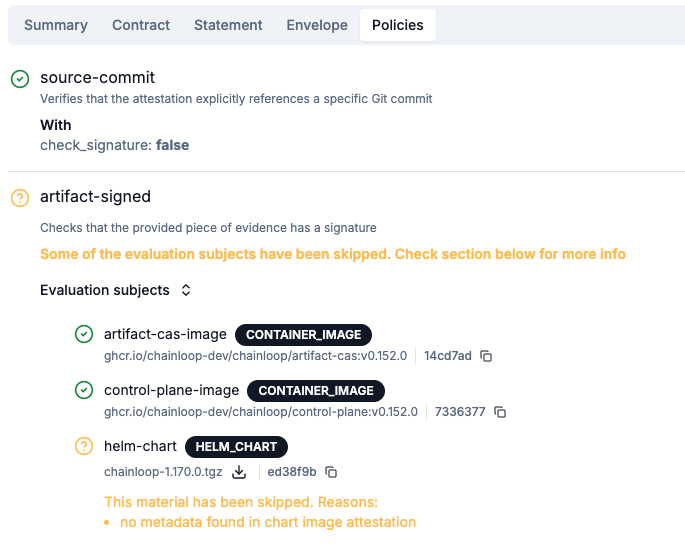
Once configured, Policies are evaluated against inputs (inputs, materials, and artifacts, will be explained in the following sections). Evaluation results will include:- Overall result: success, failure, skipped
- Policy violations: if the evaluation failed, what were the failures. For example: “component x, version y has critical vulnerabilities”
- Skip reason: if the policy couldn’t be evaluated, what’s the reason (input might have the wrong format, for example)