Summary
Chainloop CLI can sign attestations using a preconfigured SignServer instance, by providing a key reference during the signing process:Setting up SignServer
If your organization doesn’t have it already, you can follow these tutorials for a basic setup of Keyfactor’s KPI solutions:- Quick Start Guide - Start EJBCA Container with Client Certificate Authenticated Access.
- Quick Start Guide - Issue Client Authentication Certificate using EJBCA
- Quick Start Guide - Start SignServer Container with Client Certificate Authenticated Access.
https://mysignserver/PlainSigner.
Note that, at this moment, SignServer authentication is not implemented.
Signing Chainloop attestations with SignServer
Using the CLI options above, Chainloop will prepare the signed In-toto payload and send it to SignServer for signing. The returned signature is then included in the final attestation and sent to Chainloop Evidence Store for storage.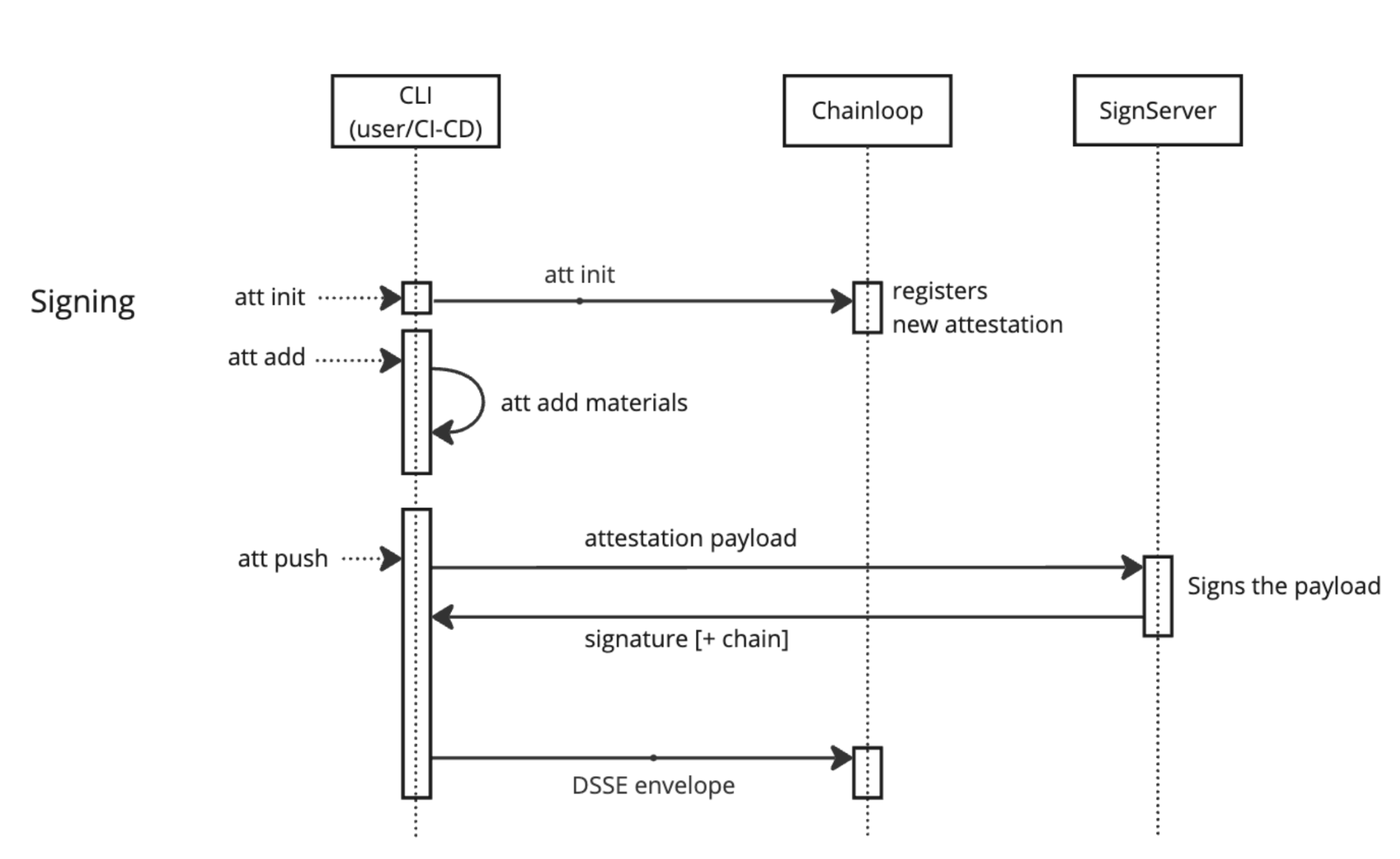
Using a TLS Client certificate for authentication
If your SignServer signer worker has been configured for client certificate authentication, you can add the flag--signserver-client-cert to the push command:

