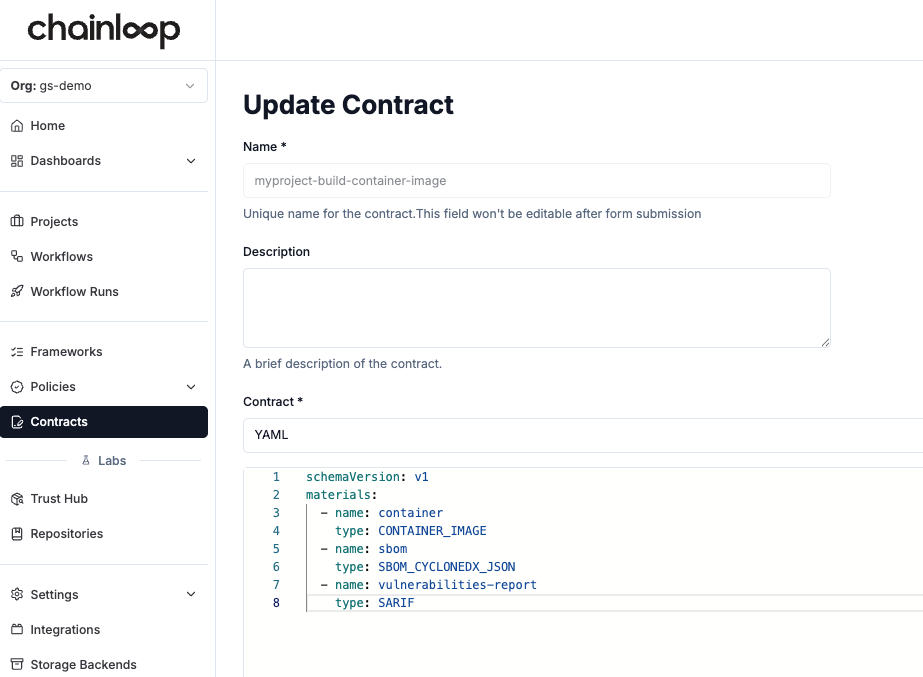
Update the contract
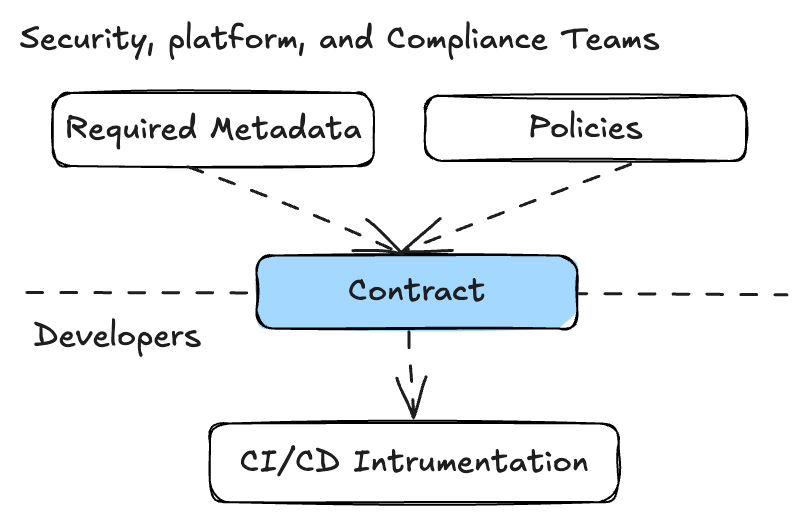
Each workflow has attached an empty contract by default, let’s update it to require a container image, an SBOM and a vulnerability report.- Web UI
- CLI
Initialize an Attestation process
Let’s perform another attestation, but note how this time the requirements have changedAdding materials and pushing the attestation.
Note that theattestation init command output this time includes a section indicating that a CONTAINER_IMAGE is required alongside with SBOM_CYCLONEDX_JSON and SARIF.
What would happen if we try to push without adding any material?
Command Output
Command Output
Note that we have specified
--name container, since that’s the material name that the contract expects. You can learn more about the adding materials process in the Adding Materials section.Command Output
Command Output
Command Output
Command Output
- Web UI
- CLI
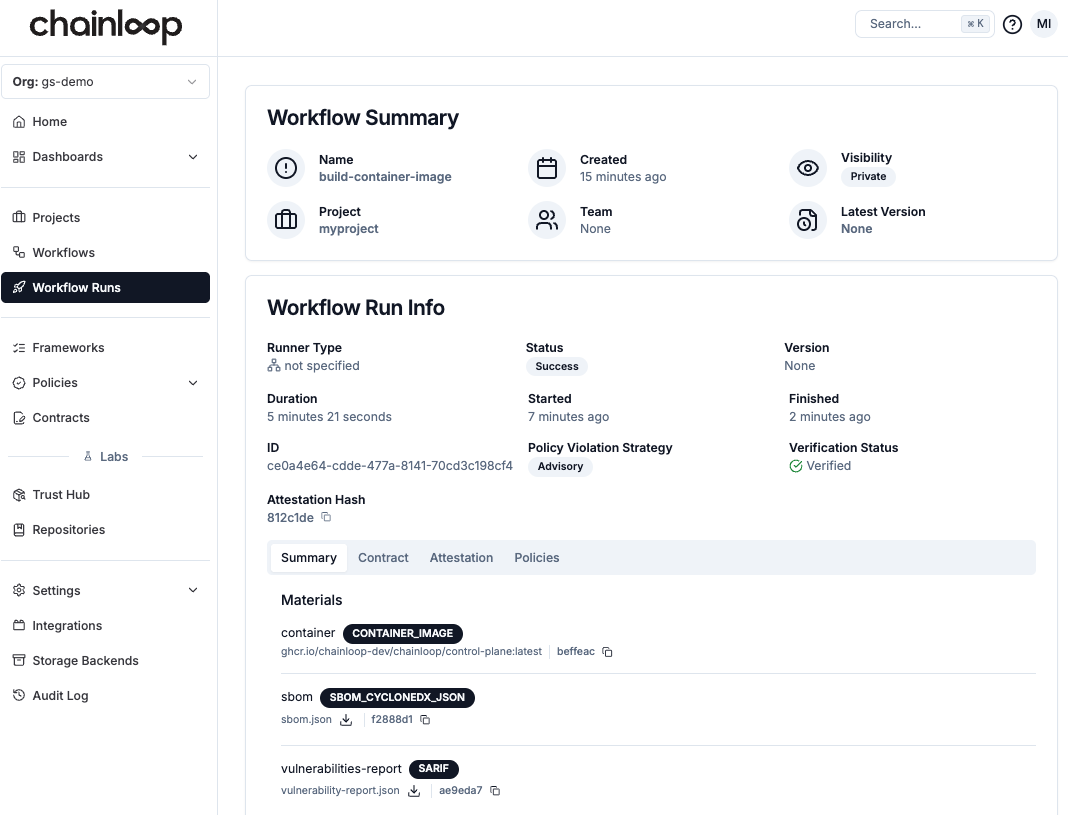
As before, we can see the details of our attestation in Chainloop Platform: