Install the Chainloop CLI
Typically attestations are created by CI/CD pipelines, but in our quickstart we’ll do it locally using the Chainloop CLI.Perform an attestation
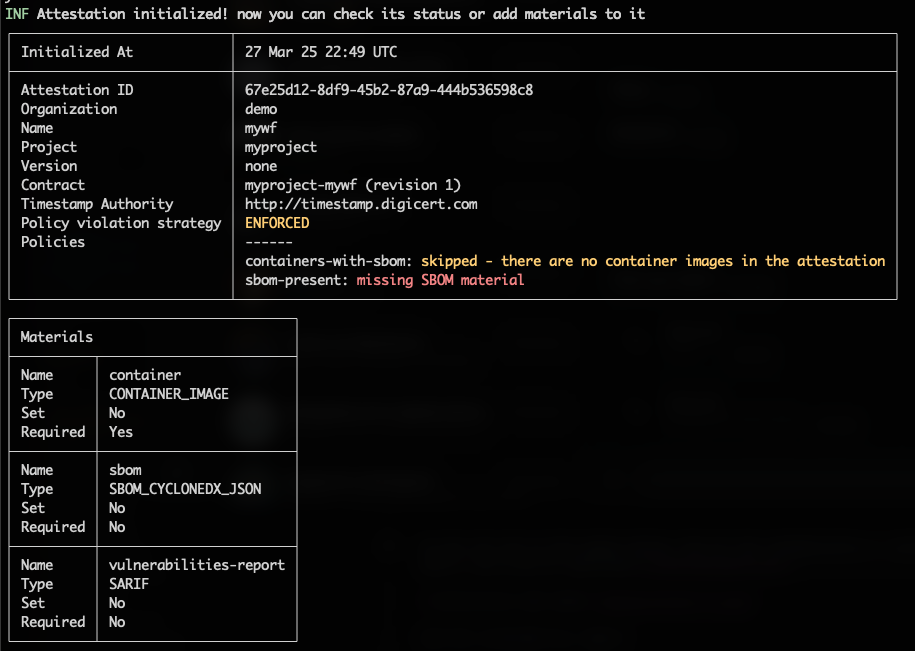
We are now ready to perform our first attestation. In a nutshell, an attestation process has three steps: initialization, adding evidence, and storage. See lifecycle for more details.Initialization
We’ll start with the initialization of an attestation. The command requires the name of a workflow, a project and optionally a contract. Copy the command that suits your environment:- Chainloop Platform
- Chainloop OSS
Add Pieces of Evidence
Once attestation is initialized, we can start adding materials to it. In this case, we are attesting the latest version of the Chainloop’s control-plane image as an example.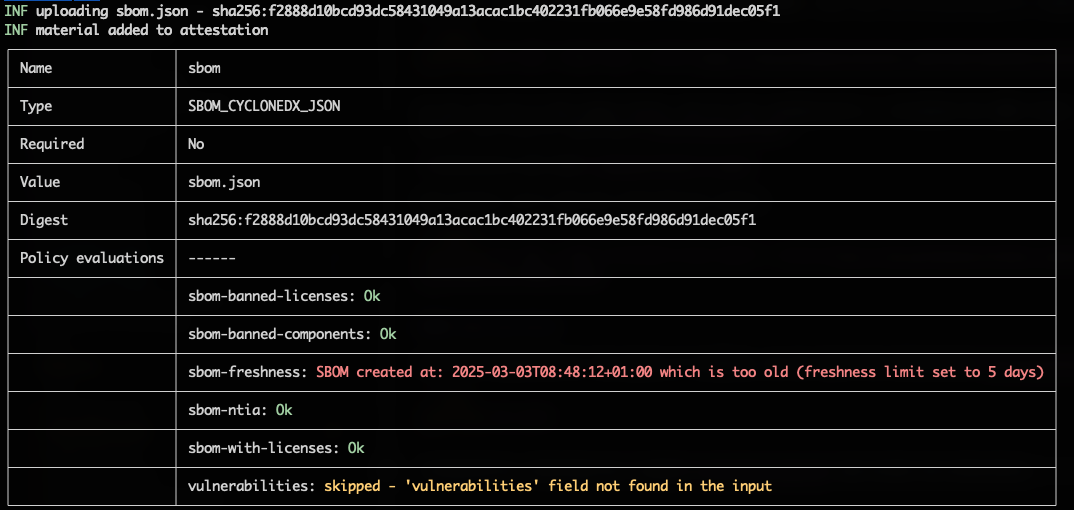
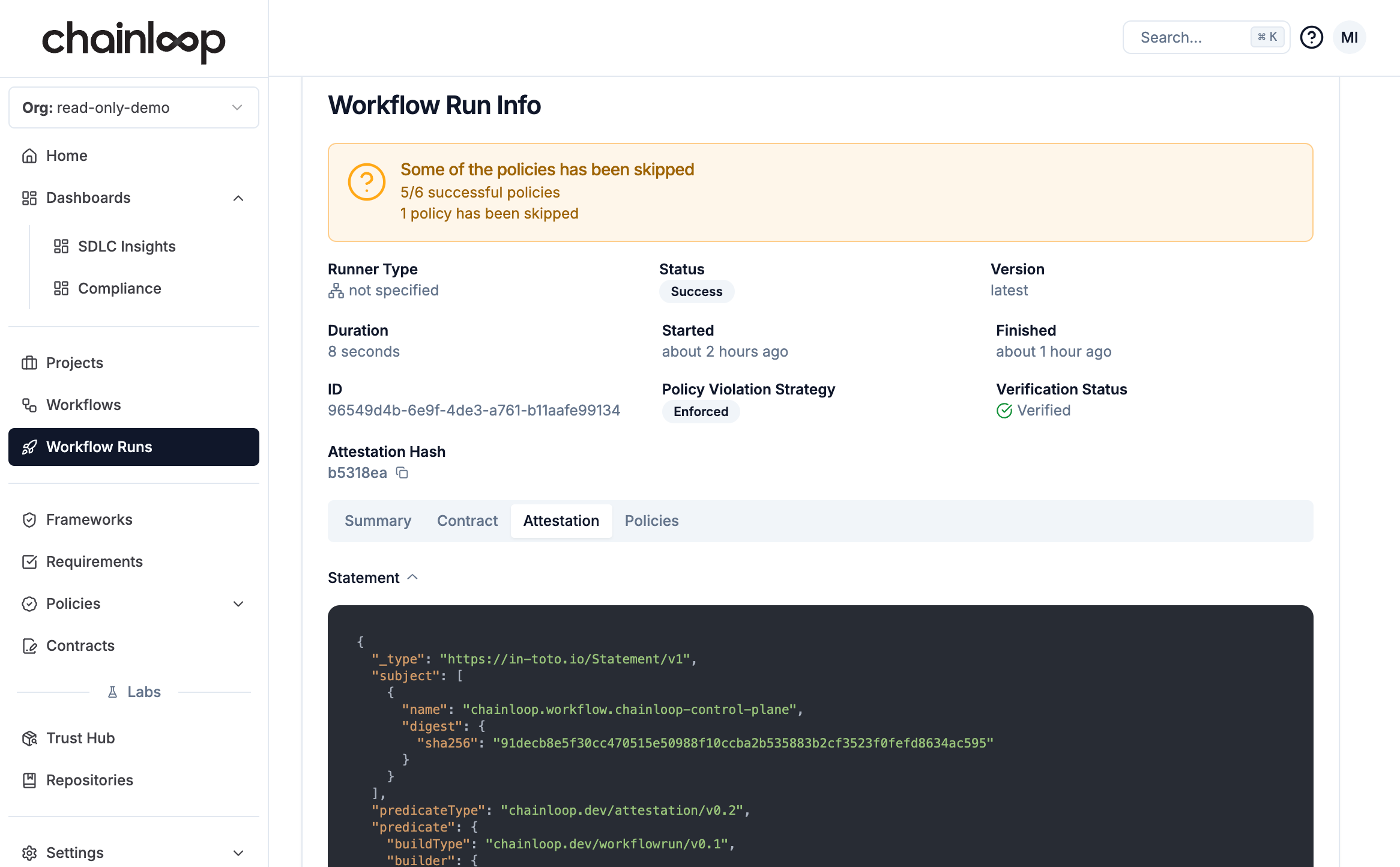
Sign and Store
Once we’ve gathered all the pieces of evidence, we can push the attestation for permanent storage.- Web UI
- CLI
You can find your attestation in the workflows section.