Authentication
First, you need to authenticate the CLI to Chainloop service. Currently we support two authentication methods during the attestation process, user authentication and API key authentication, for this step we’ll use the user authentication, which can be done by running the following command:Initialize the Attestation process
In a nutshell, an attestation process has three steps: initialization, adding evidence, and storage. Refer to this section to learn more about the attestation lifecycle. We’ll start by initializing an attestation. The attestation process requires the name of a workflow and a project to associate with it. Chainloop workflows represent any CI or process that you want to attest. Projects and project versions represent your software product lifecycle.Command Output
Command Output
Add Pieces of Evidence (a.k.a materials)
Once the attestation process is initiated, we can attach as many pieces of evidence as we want. In this case, we are adding a reference to a container image. Many other material types are supported - check the supported list.Command Output
Command Output
Command Output
Command Output
Sign and Store the Attestation
Finally, we sign and push the attestation to Chainloop for permanent preservation using.Command Output
Command Output
Inspect the Attestation
Congratulations! We’ve performed our first attestation, now we can head to the workflow runs section in the platform UI and inspect the attestation we just created.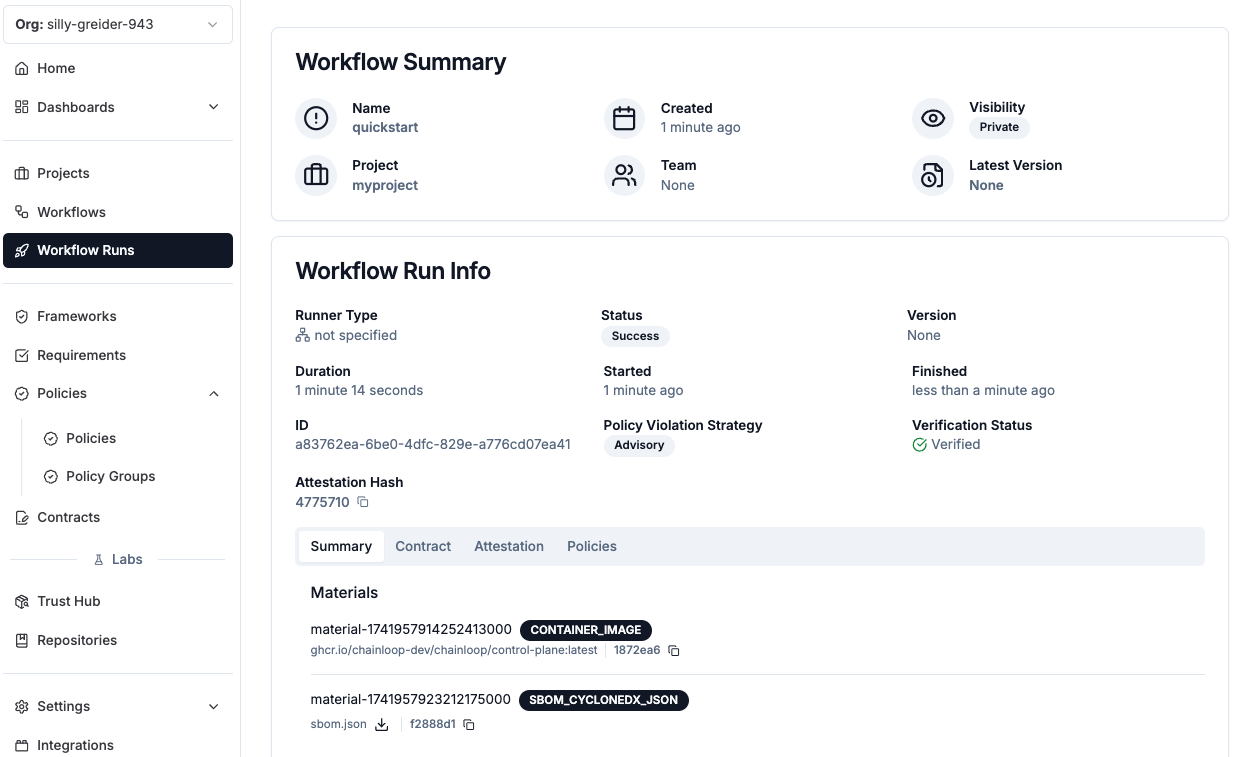
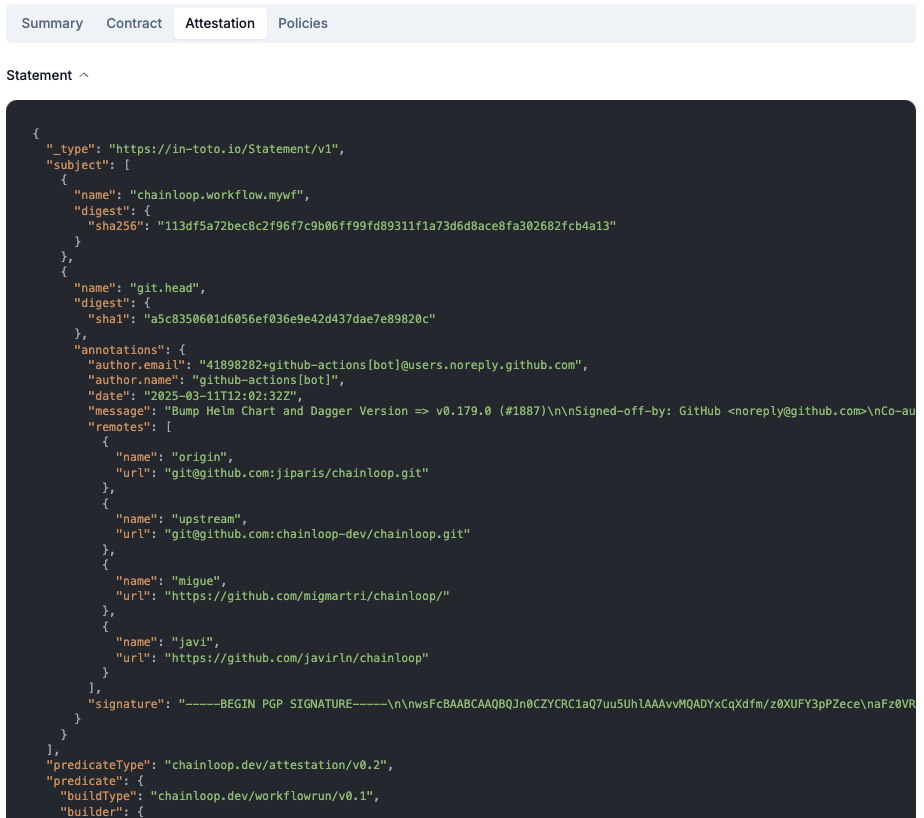
Verifying your attestation
You can verify the integrity of the attestation by downloading the bundle (in Sigstore format) and running the verification command.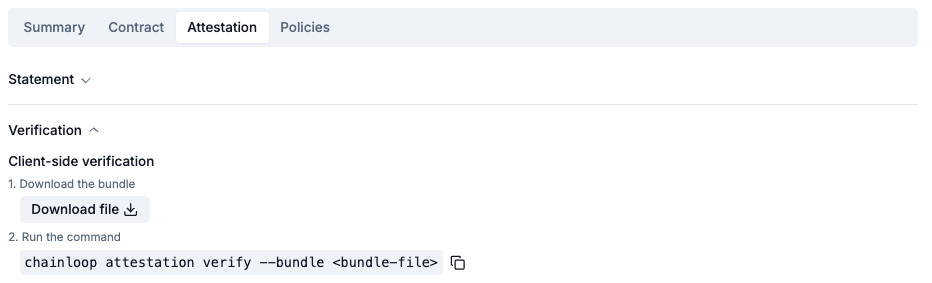
- Checking the validity of the signing certificate included in the bundle, against the Chainloop trusted root
- Checking the validity of the timestamp signature
- Verifying the payload integrity (the in-toto attestation included in the bundle) and its signature.

