Data Gathering Primitives
Material
In Chainloop, a material is any piece of evidence (metadata) generated as part of the software development lifecycle (SDLC), or in more general terms, in any activity from the company compliance process. Examples of materials are:- A container image built in a CI pipeline, referenced by its OCI URL (oci://my-registry/my-repo@mytag)
- A software bill of materials (SBOM)
- A test or code coverage report
- A vulnerability scan result
- An infrastructure scan, and more
Attestation
An attestation is a unit of data sent to Chainloop. Users and CI systems use the Chainloop CLI to “craft” attestations, add pieces of evidence (materials) to them, and “push” them to Chainloop service (the evidence store). Attestations are performed with the Chainloop CLI and its lifecycle looks like thisWorkflow
A workflow represents a source of data to be sent to Chainloop. It usually corresponds to a CI pipeline, but it doesn’t necessarily need to match. For example, users might send data from other sources, like a custom integration from Jira. Workflows are just an umbrella term for all data ingestions from the same source. Read the docsWorkflow Run
A workflow run represents an execution of a workflow. A successful workflow run will be associated with an attestation. Read the docsContract
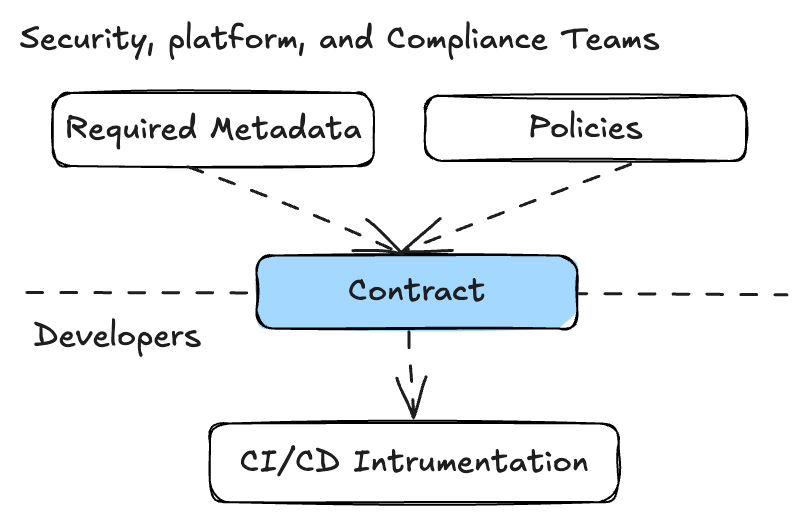
Compliance Primitives
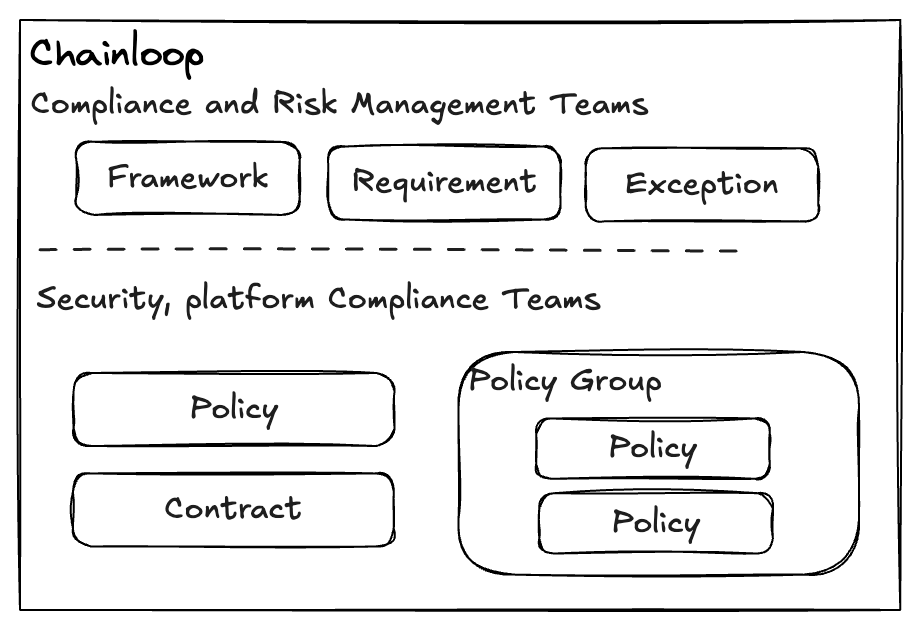
Policy
Policies are rules evaluated against materials and/or the whole attestation document. They represent acceptance criteria for the system to ingest those materials. Even in failure cases (when there are policy violations), attestations are still sent to Chainloop but clearly marked as “not compliant.” This way, Chainloop keeps track of everything that is happening in the system, even if it’s not acceptable. Policies are written in Rego language. Read the docsPolicy Groups
Policy groups are a way to group policies together. They are used to be able to attach a set of policies to a workflow contract. Read the docsFrameworks
Frameworks represent high-level regulatory standards or good practices. They are usually promoted by governments and required for companies to fulfill, such as SDDF, SOC2, CRA, etc. Frameworks can also represent internal, custom checklists and normative for release management, security compliance, etc. In any case, Chainloop will help automate those by giving tools to manage and automate frameworks and requirements in terms of policies and data ingestions. Read the docsRequirements
Requirements are a high-level representation of Compliance criteria that the project must meet. They are not necessarily technical but written in high-level natural language by Compliance teams. It’s the responsibility of SecOps teams to map high-level requirements into low-level policies. Requirements are grouped in a framework. Read the docsExceptions
Sometimes, it’s acceptable for some organizations to release software without fulfilling all internal requirements. In these cases, Chainloop provides a way to register “exceptions” to those requirements, marking them as exempt and thus not counting against compliance criteria. Exceptions and their authors are recorded in the system for future auditing. Read the docsOrganizational Primitives
Organization
Organizations represent the tenant entity in Chainloop. All users belong to one or more organizations and might have different role levels.- Web UI
- CLI
You can select or create an organization in the top left corner of the Chainloop Web UI.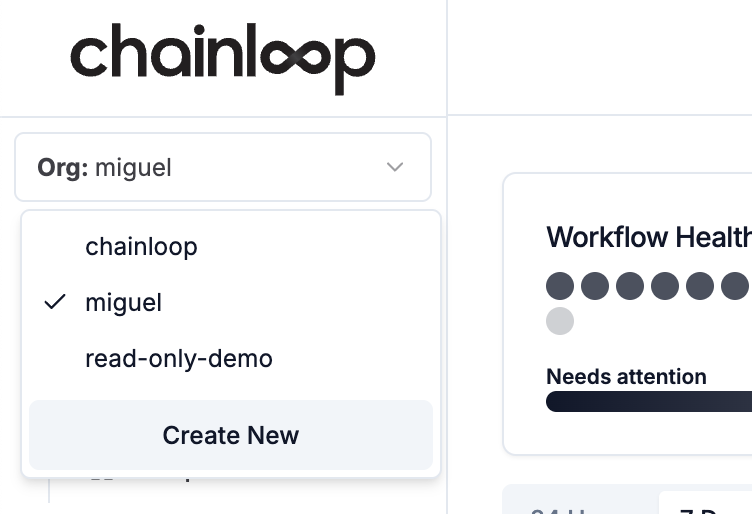

Business Units
This feature is only available on Chainloop’s platform paid plans.
Products
This feature is only available on Chainloop’s platform paid plans.

